Zero-Trust Network Access Demo
Experience the future of secure access with a live ZTNA demo
Key components of this demonstration
Visualize the authentication process for employees on campus or remote locations.
Explore secure access controls that grant user profile-based access to business apps.
Strengthen web access control with thorough monitoring of all internet traffic.
Enter your details to view
One step away
from a gold mine of resources
Enter your details to view



Experience seamless & secure access
With Tata Communications ZTNA experience cutting-edge access controls in action, featuring secure user validation, device trust assessments, and tailored access to critical applications.
Experience seamless & secure access
With Tata Communications ZTNA experience cutting-edge access controls in action, featuring secure user validation, device trust assessments, and tailored access to critical applications.
User authentication & management
-
Visualise secure identity verification with MFA – easy to add remove users & apply real time policies.
Posture check & verification
-
Validate device compliance and security posture before granting access to critical workloads.
Granular application-specific access
-
Enable precise access to authorized applications, minimizing risks and boosting productivity.
Tailored to fit. Managed to deliver
Our experts design, deliver and manage your chosen SASE stack using the AXIOM™ methodology
Connect
20% improved performance with end-to-end carrier-grade connectivity.
Core Activities
- Discovery workshops and structured POCDiscovery workshops and structured POCDiscovery workshops.
- Discovery workshops and structured POCDiscovery workshops and structured POCDiscovery workshops.
Protect
Real-time threat protection with 8k+ IOCs identified and blocked daily.
- Discovery workshops and structured POCDiscovery workshops and structured POCDiscovery workshops.
- Discovery workshops and structured POCDiscovery workshops and structured POCDiscovery workshops.
Simplify
Single-pass architecture improving end-to-end visibility and context-led insights.
- Discovery workshops and structured POCDiscovery workshops and structured POCDiscovery workshops.
- Discovery workshops and structured POCDiscovery workshops and structured POCDiscovery workshops.
AXIOM™
99.8% first time-right deployment, with the flexibility to choose between single or multi-vendor SDWAN and SSE, augmented by our expert design, deliver and managed services.
- Discovery workshops and structured POCDiscovery workshops and structured POCDiscovery workshops.
- Discovery workshops and structured POCDiscovery workshops and structured POCDiscovery workshops.



.jpg)
A partner you can trust

Managed Service Provider of the Year for SASE and SD-WAN at MEF’s NaaS Excellence Awards


Leaders in network – Software defined solutions and services & SASE - APAC


Leaders in the 2024 IDC Asia-Pacific Managed SD-WAN and SASE Services Marketscape


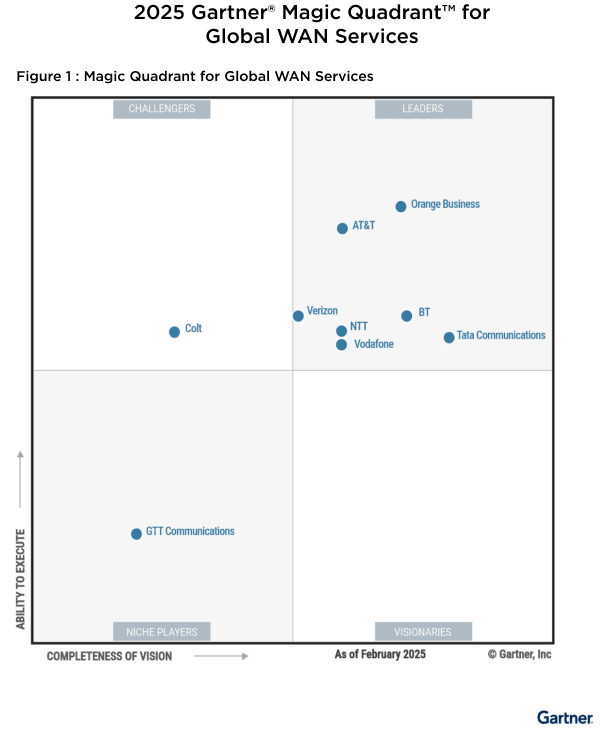
Recognised by Gartner as a leader in the Gartner Magic Quadrant for Global WAN Solutions

Blog
VPN vs. ZTNA: Comparing traditional and modern secure access

Blog
CASB vs. ZTNA: Comparing cloud and network security
.jpg?width=2000&name=shutterstock_1440345497%20(1).jpg)
Blog
ZTNA vs. SASE: Comparing next-generation security frameworks

Blog
Understanding ZTNA architecture: Building blocks for zero trust security
.jpg?width=2000&name=shutterstock_2442146479%20(1).jpg)
Blog
VPN alternatives : Risks, challenges, & modern alternatives
.jpg?width=2000&name=shutterstock_2285412737%20(1).jpg)
Blog
Zero Trust Network Access (ZTNA): Features, implementation & best practices

Blog
SASE and Zero Trust: The Perfect Partnership for Modern Security

Blog
ZTNA vs VPN & SD-WAN vs MPLS: The ultimate showdown for enterprises
What’s next?
Explore Our Solutions
Engage with interactive demos, insightful surveys, and calculators to uncover how our solutions fit your needs.
Exclusive insights
Get exclusive insights on the Tata Communications Digital Fabric and other platforms and solutions.