Discover strategies to make your SOC agile, secure, resilient, and ready for today’s evolving threat landscape.
Rapid setup. Fast threat detection. Swift response.
Protect your IT/OT infrastructure with our industry-leading Managed Detection and Response Solution.
Are you prepared to tackle increasingly sophisticated threats head-on?
.jpg)
Lack of skilled resources and legacy technology
Many enterprises lack the time, effort, and expertise to monitor and detect security threats and respond to security incidents 24/7. This challenge is compounded by the dependency on legacy technology in the absence of a modern SOC.
.jpg)
Speed and complexity of cyberattacks
Enterprises are often caught off-guard by the sheer volume of security threats, leaving them little time to identify and mitigate incidents successfully.
.jpg)
Lack of visibility into the attack surface
A dynamic digital landscape means a larger attack surface. The lack of a unified threat visibility across a fragmented landscape, the absence of centralised reporting, and advance analytics leave gaping holes in threat detection and mitigation.
.jpg)
Lack of security measures to combat unknown or emerging threats
Even the best plans fall flat in the face of sophisticated threats coming from different directions. This makes the need effective security measures more pressing than ever.
.jpg)
Operational efficiency
Without integrated log monitoring, security analytics and native SOAR, operational efficiency takes a hit, leaving enterprises more prone to security incidents.
.jpg)
Alert fatigue
A high volume of false positives poses a huge challenge to the SOC, hindering its ability to differentiate critical threats from minor issues and fails to respond at speed
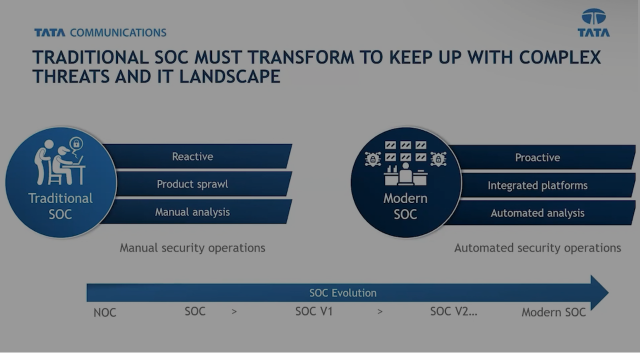
Cutting-edge MDR, for a sophisticated threat landscape.
Leverage advanced analytics, machine learning, and expert-led operations to detect, investigate, and neutralize threats, faster. Gain round-the-clock visibility, guided action, and scalable protection.
.jpg?width=4000&height=2369&name=mdr_infographic_desktop%20(1).jpg)

Explore our solutions
.jpg?width=300&height=200&name=shutterstock_2602293623%20(1).jpg)
Security Information and Event Management (SIEM)
Security-as-a-service with centralised, cloud-based SIEM delivers a single-pane view of threats mapped to MITRE ATT&CK with 800+ engineered use cases for advanced threat detection.
.jpg?width=300&height=200&name=shutterstock_2574781227%20(1).jpg)
Security Orchestration, Automation, and Response (SOAR)
60+ SOAR playbooks for automated triaging and response that secures the enterprise against advanced persistent threats, and reduces administrative complexity, as well as cost and mean time to respond.
.jpg?width=300&height=200&name=shutterstock_2160176449%20(1).jpg)
Next-gen SOC
Enhanced detection and response services empowered by AI, ML and automation capabilities reduce the mean time to detect, qualify, prioritise and respond to multi-stage attacks significantly.
.jpg?width=300&height=200&name=shutterstock_2539085027%20(1).jpg)
User and entity behaviour analytics
Create standard profiles and behaviours across time and peer groups and highlight anomalous activities, detecting malicious insiders and external attackers to avoid potential incidents.
.jpg?width=292&height=200&name=shutterstock_2204100815%20(1).jpg)
Advanced endpoint security service – EPP and EDR
Advanced threat management services offering 24/7/365 monitoring and management of endpoint security.
.jpg?width=300&height=200&name=shutterstock_2133712651%20(1).jpg)
Cyber threat intelligence (CTI)
Our proprietary CTI platform collects and analyses data from 65+ disparate sources, including our own global NetFlow data, to deliver relevant threat intel feeds with visibility into the latest high-fidelity indicators of compromise (IOC).
.jpg?width=379&height=200&name=shutterstock_2587460659%20(1).jpg)
Threat Advisory
Specialised services that provide contextualised weekly CTI advisories covering latest threats, vulnerabilities, targeted campaigns, and more, across industries and geographies.
.jpg?width=300&height=200&name=shutterstock_2497223349%20(1).jpg)
Deception-as-a-service
Deception technology detects the stealthiest cyber-attacks by creating a knowledge gap for attackers and tricking them into traps. Understanding what attackers desire creates the opportunity for an active, intelligent defence that lures, detects, and defends.
.jpg?width=356&height=200&name=shutterstock_2645806005%20(1).jpg)
Threat hunting and incident response retainer services
Automated, rule-based, and hypothesis-based proactive detection and isolation of malware and other evolving threat vectors to reduce a breach’s cost, damage, and impact.
.jpg?width=300&height=200&name=shutterstock_2376133957%20(1).jpg)
Brand monitoring, dark web and executive monitoring, and anti-phishing services
Cyber threat management services like proactive brand monitoring to prevent potential brand abuse.
Discover how our integrated solution proactively detects advanced threats, and automates responses to secure your IT and OT infrastructure.
Keep up with the latest updates in cybersecurity via our weekly Threat Intelligence Advisory.
Our intelligence reports uncover emerging threats, highlight vulnerabilities, and offer critical insights and actionable steps to strengthen your cyber defences.
.jpg?width=542&height=305&name=shutterstock_2461670657%20(1).jpg)
Address remote work & cloud security risks with MDR

1
Increasing attack surface with remote work & cloud adoption
Organisations with remote workforce, hybrid cloud environments, and IoT devices need MDR to continuously monitor endpoints, cloud workloads, and networks for threats.
2
Cost challenges that compromise security
From being unable to hire expensive cybersecurity talent to lacking the budget for a full-fledged Security Operations Centre, the lack of resources often leads to gaping holes for potential threats.
3
Reducing false positives to strengthen threat defense
Often, enterprises find their SIEM overloaded with false threats, leaving their IT and OT infrastructure vulnerable to real attacks across their dynamic digital landscape.
The Tata Communications MDR advantage
14 days
Rapid SOC deployment timeline
99%+
Improvement in MTTD and MTTR
400+
MITRE ATT&CK aligned use cases
Count on us for proven results
.png?width=135&height=130&name=osn-logo%20(1).png)
CASE STUDY
How we bolstered OSN's security infrastructure, enabling faster threat detection, reduced costs, and uninterrupted service for millions of viewers.

CASE STUDY
Kotak Mahindra Asset Management Company (KMAMC) enhanced its cybersecurity resilience with Tata Communications Managed SIEM, SOAR, and UEBA solutions, achieving real-time threat visibility, automated responses, and improved governance.
CASE STUDY
Discover how Bajaj Auto Credit Limited (BACL) swiftly launched a compliant digital loan platform within 60 days, achieving 99.999% uptime and a 30% month-on-month growth in platform utilization.

Srikanth Apanna
CTO, BACL
"Tata Communications delivered a comprehensive solution, including a robust digital platform, Data Centre, and Disaster Recovery setup, all tailored to meet our stringent requirements."

Tom Jones
VP, Broadcast & Digital Operations, OSN
"This partnership allows us to focus on our core business while protecting premium content and the user experience from emerging cyber threats."
A partner you can trust
Cyber Security Excellence Awards Winner: Proactive MDR for Advanced Threat Protection

Our latest resources
Frequently asked questions
What are brute force attacks?
How to identify and avert Backdoor Attacks?
What is WannaCry Ransomware?
What kind of Ransomware is Locky?
What is CLOP Ransomware?
What’s next?
Experience our solutions
Engage with interactive demos, insightful surveys, and calculators to uncover how our solutions fit your needs.
Exclusively for you
Stay updated on our Security Fabric and other platforms and solutions.



