IDC’s Research Director, Cathy Huang, shares key SSE adoption phases, buyer tips, and how to pick the right partner for a smooth, first-time-right transition.
Seamless security for borderless enterprises
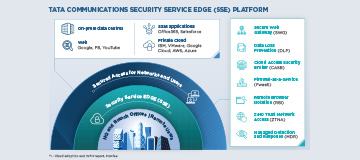
Secure private apps, users, and internet traffic with an integrated, managed, and cloud-native Security Service Edge.
Challenges most enterprises face when it comes to scalable security
Protect remote and hybrid work force
Legacy VPNs and network-level controls like IP tables and ACLs are no longer effective in a work-from-anywhere world. They increase complexity, slow performance, and expose organisations to lateral threats across an expanded attack surface.
Secure cloud migration
Cloud migration raises concerns due to inconsistent security across multi-cloud setups, limited visibility, and complex management, especially when handling regulated data through multiple Cloud Service Providers (CSPs).
Accelerate move to SASE
Traditional MPLS-heavy networks and fragmented security architectures can’t meet the needs of always-on, digital-first enterprises, navigating hybrid, multi-vendor environments.
Gauge your enterprise’s readiness for
Security Service Edge.
Take the 10 minute SSE maturity test and uncover strength and gaps in your strategy.
Simplify security with our cloud-native SSE solution
Secure private apps, users, and internet traffic with an integrated, cloud-native Security Service Edge. Enhance security, visibility, control, and performance with Tata Communications SSE.
Single-vendor, unified SSE platform
Leverage superior threat visibility and analytics to reduce product sprawl, tackle operational inefficiencies and bridge gaps in visibility.
Quick and agile implementation
Achieve faster time-to-value with our Golden Templates and proven SSE frameworks that help you deploy enterprise-wide security quickly, with first-time-right implementation.
Act fast against emerging threats
Respond to threats within seconds with Tata Communications TCx, our unique platform, powered by advanced correlation and analytics that help simplify management and reduce mean detection time.
Continuous management and optimisation
Maximise security with our dedicated 24/7 centre of excellence, where 1,400+ SSE-certified experts deliver continuous SSE optimisation, rigorous testing, and support for new use cases.
.jpg?width=2000&name=shutterstock_2463474605%20(1).jpg)
Secure web gateway
Ensure safe use of web and web-based applications for your users and employees by proactively monitoring application availability and uptime. Prevent attacks from sophisticated threats such as ransomware and malware.
.jpg?width=2000&name=shutterstock_2526834797%20(1).jpg)
Gateway to SASE
Plan your SSE journey with a broader SASE vision, unifying single-vendor SSE and SD-WAN in a seamless, Hosted SASE solution designed to uncomplicate and transform your business.
.jpg?width=2000&height=1125&name=shutterstock_2128052546%20(1).jpg)
Secure private access
Implement identity and network segmentation aligned to Zero Trust Network Access tenets of NIST while balancing user experience with adaptive authentication.
.jpg?width=2000&name=shutterstock_2500549895%20(1).jpg)
Cloud access security broker
Secure cloud application access and usage by enforcing enterprise security policies to run appropriate checks and controls. Ensure robust data protection with protective and detective controls for cloud.
.jpg?width=2000&name=shutterstock_2164696373%20(1).jpg)
Data Loss Prevention (DLP)
Ensure your organisation’s sensitive data is not accessed by unauthorised users, stolen, or lost. Monitor data flow and prevent potential breaches and data exfiltration.
.jpg?width=2000&name=shutterstock_2210384985%20(1).jpg)
Remote Browser Isolation (RBI)
Protect users against browser-based security threats, zero-day malware and APT attacks, by isolating web traffic between the user’s device and browser-based malware.
.jpg?width=2000&name=shutterstock_2465677723%20(1).jpg)
Managed Firewall and UTM
Get continuous 24/7/365 protection against unauthorised network access across your on-premises and cloud IT estate with a fully managed next-generation firewall (NGFW) and UTM solution.
End-to-end SSE. Delivered expertly.
Our experts design, deliver and manage SSE using our proven AXIOM methodology.
Assess
Build a strategic SASE adoption roadmap through a structured assessment of current vs. future state.
Core activities
- Discovery workshops and structured POC
- Infrastructure analysis
- Deployment roadmap
VAS packs
- Secure network transformation roadmap
- Digital-twin
eXecute
Achieve seamless migration and robust integration. Ensure precise alignment and thorough testing.
Core activities
- Pilot site/user validation
- Project planning and scheduling
- Hardware delivery and installation
VAS packs
- Dedicated program management
Integrate
Achieve seamless migration and robust integration. Ensure precise alignment and thorough testing.
Core activities
- Installation and configuration management
- Integration and migration approach
- Hardware delivery and installation
- Testing and validation
VAS packs
- Migrate
- Secure*
- Headend install
Operate & Manage
Continuously improve, control, and optimise for best performance.
Core activities
- Periodic policy optimisation
- Feature-rich customer portal
- Automated fault diagnosis
- Proactive network monitoring
VAS packs
- mBYON
- ProCare*




Explore use cases
1
Secure cloud-first environments at scale
Enterprises migrating to SaaS applications require cloud-native security. Traditional VPN-based security proves insufficient for cloud-first environments, requiring ZTNA for secure access.
2
Meet regulatory demands with confidence
Ensure regulatory compliance with DLP, CASB, and policy-based encryption. Gain visibility into shadow IT and unauthorised cloud usage.
3
Protect data and transactions in real-time
From customer data and trading platforms to remote financial services, secure everything with ZTNA. Ensure compliance with PCI-DSS, GDPR, and ISO 27001 using DLP and encryption.
How SSE compares against traditional security
The Tata Communications SSE advantage
50k
Users enabled with secure hybrid work
Tata Communications TCX
Provides visibility into threats across the landscape
>9.5Bn
Potential threats analysed daily via native SOAR integration
Proactive protection
Integrated cyber threat intelligence to block threats real-time
750+
Certifications across our highly skilled team of experts
24/7
Support to hundreds of customers across industries
40+
Use cases and features tested at our COE for SSE innovation
Count on us for proven results

CASE STUDY
Connecting Liberty General Insurance’s remote offices securely. Discover how our SSE solution delivered seamless site connectivity and outstanding customer service.
A partner you can trust

Leader: ISG Provider Lens for Network, Software Defined Solutions, and Services APAC (SASE & SDWAN)


Triple triumph: Global InfoSec Awards


Twin victory: MEF’s NaaS Excellence Awards

SSE solution that evolves with your changing needs

Explore Other Solutions
.jpg?width=2000&name=shutterstock_1959377737%20(1).jpg)
IZO™+ SD-WAN
Transform your network and security architecture with a managed service that combines SD-WAN and network security.
.jpg?width=2000&height=1125&name=shutterstock_2487049861%20(1).jpg)
Managed SASE
Simplify, secure, and scale network access with Tata Communications SASE solutions that integrates SD-WAN and Security Service Edge (SSE) into a unified, cloud-native platform, offering enterprises enhanced security, streamlined network management.

Zero trust Network Access (ZTNA)
Move beyond VPNs to cater to your remote workforce’s security and performance demands, while safeguarding vital assets.
Our latest resources

Analyst Report
Best Practices for Successful Secure Service Edge Deployment
Explore key insights on how enterprises can successfully implement Secure Service Edge (SSE) to ...
What’s next?
Explore Our Solutions
Explore our solutions through immersive platform demos or engage with our surveys and pricing calculators
Exclusive insights
Get exclusive inisghts on our Network Fabric and other platforms and solutions